Possibly the primary estate where your business’s revenue is generated.
But also, the number 1 target for threat actors. We combine all our other services into this one domain for your peace of mind.
Whether you are in the cloud, or on-prem, or on both, secure network design principles, architectures and controls apply uniformly. You need to protect your publicly accessible services against abuse
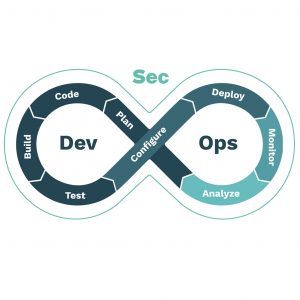
With DevSecOps, security is not treated as an isolated process or separate feature, but rather as an integral part of your development lifecycle. We work with and deploy the best tools and processes the biggest cloud vendors provide to help you secure your code and software supply chain through automation.

Identify vulnerabilities in your code with automated security alerts or when credentials and tokens are mistakenly committed into source control. Our team take the hassle out of your hands by configuring the scans, interpret them and provide mitigation advice. We can even operationalise the entire process for you and let you solely focus on building new features for your customers.

Scan container registries using Azure’s Microsoft Defender or Amazon’s Elastic Container Service. Identify and act on access management, infrastructure and compliance issues by letting us configure and deploy either cloud native or best-in-class 3rd party solutions. We provide secure configuration to containers to minimize attack surface areas. Let us do the tough work, so you don’t have to
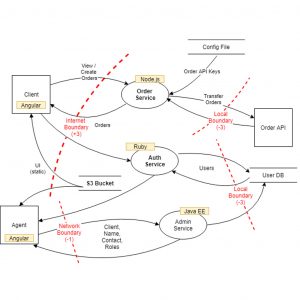
Threat modelling is used to identify threats, attacks, vulnerabilities, and countermeasures that could affect your application. Through a series of work shops, we guide you through the phases of: defining security requirements – Creating an application diagram – Identifying threats – Mitigating threats – Validating threats have been mitigated.
